Can your authentication really verify the person? Introducing Identity-Bound Biometrics
Identity-Bound Biometrics (IBB) creates a unique biometric identity to verify the person taking action, so you can be confident that only the correct, approved users are accessing your systems or critical data.
IBB goes beyond traditional authentication based on "something you have" or "something you know".
IBB authenticates "something you are".
Phone-less. Token-less.
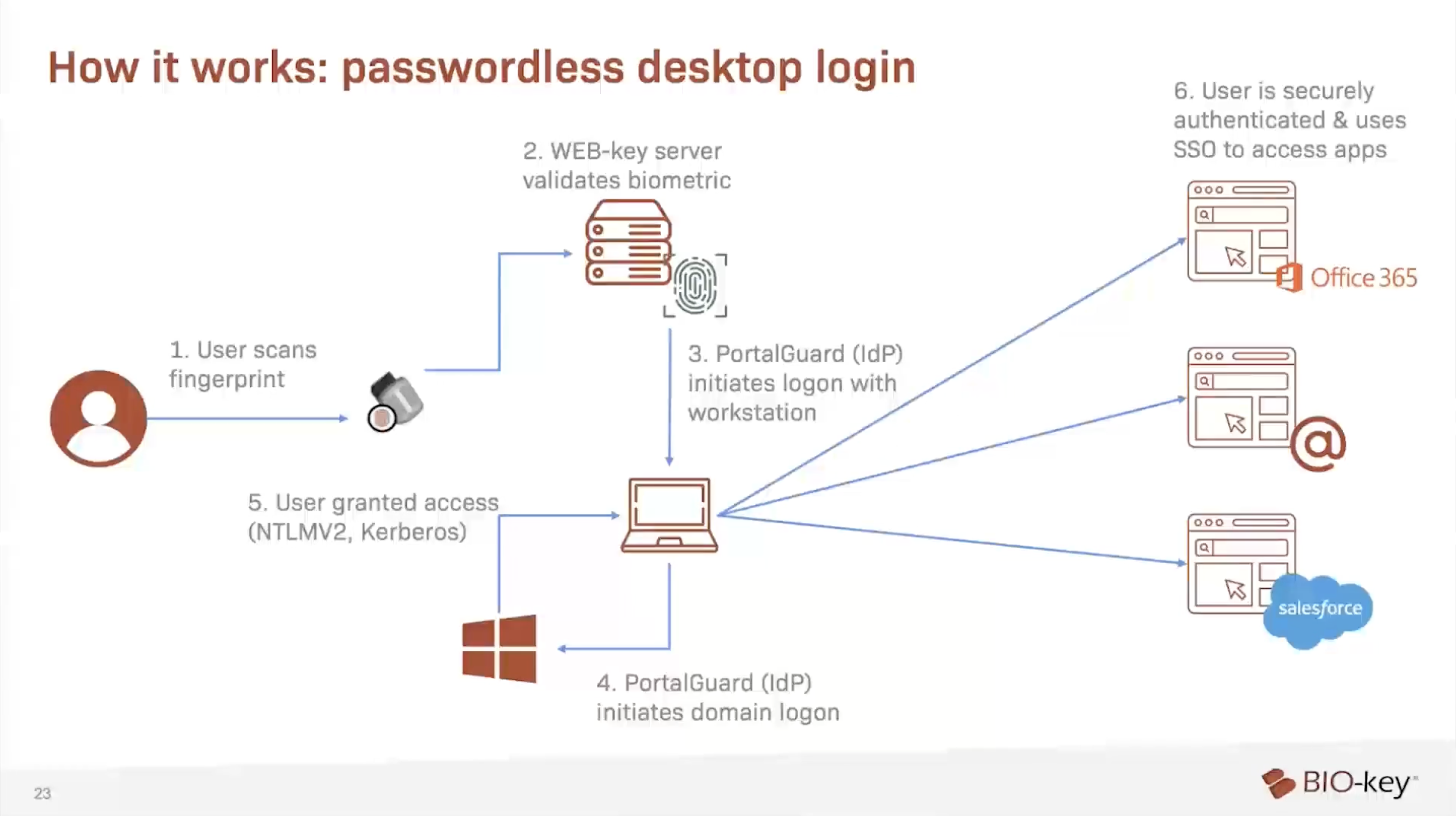
Go Passwordless with IBB
Passwordless authentication with IBB uses the person as the credential for authentication — no phones or tokens required. It is the safest, most efficient, most cost-effective, and most secure option for a range of scenarios and business-critical operations across industries.
Other Use Cases for IBB
Customer Testimonials

"Our team at Orange Bank is partnering with BIO-key to provide our financial institution with a cloud IDaaS solution that delivers advanced biometric authentication. BIO-key provides both biometric authentication and a proven suite of IAM solutions that provide security flexibility and value over approaches offered by other vendors."
Kathy Pinto
VP of IT, Orange Bank & Trust

"Based on our search for an enterprise IAM solution that provided secure passwordless authentication and met US Government compliance requirements, we can validate the significant value provided by the PortalGuard IAM platform and biometric capabilities over other vendors."
William Elks
IT Manager, YYK Enterprises
Award-Winning Identity & Access Management Solutions
PortalGuard is a single, unified Identity and Access Management platform (IAM) trusted by over 1,000 global customers across industries to meet the highest security goals. PortalGuard provides flexible solutions to a range of use cases and business initiatives and is the only IAM platform offering IBB.
The one-of-a-kind multi-factor authentication app that brings the power of Identity-Bound Biometrics to any mobile device.
About BIO-key
With over two decades of expertise, BIO-key is revolutionizing Identity Access Management (IAM) with solutions powered by the security of Identity-Bound Biometrics that authenticates the identity of all users with the highest level of integrity and streamlines access across devices and applications.
BIO-key’s award-winning IAM solutions are trusted by over 1000 customers worldwide to:
◘ Meet cyber insurance requirements
◘ Eliminate passwords
◘ Secure remote access & workstations
◘ Protect against cyberattacks
◘ Streamline workflows
◘ Improve productivity for the IT team
For more information, please don't hesitate to contact us to discuss your requirements.
Contact Us Form
Awards & Recognition
"We are so proud to name BIO-key PortalGuard as a winner in the 2022 Fortress Cyber Security Awards program. As our society continues to evolve and become more reliant on networks and data, companies like BIO-key are critical at providing the protection and trust consumers demand."
Maria Jimenez, Chief Nominations Officer, Business Intelligence Group
"We selected PortalGuard as ‘Identity Management Solution of the Year’ for how easily it helps customers secure access for both the workforce and customers while also giving organizations peace of mind that they know who is gaining access regardless of their location."
Bryan Vaughn, Managing Director of RemoteTech Breakthrough Awards



.png)



.png)
.png)
.png)
.png)

Additional Resources
Here are some cybersecurity resources you might find useful or check out our Resource Center for all content.

eBook
Ranking Authentication Methods
An in-depth guide analyzing and evaluating different methods of authentication supported by the BIO-key enterprise IAM solution.

Whitepaper
Why Zero Trust is Important
Explore how organizations are deploying a zero trust architecture, and the best practices and solutions to support zero trust.
Case Study
Orange Bank & Trust Company
Discover how the Orange Bank & Trust Company improved its authentication strategy with MFA and Identity-Bound Biometrics.
Webinar
Phone-less. Token-less. Passwordless.
Find out where the most common passwordless authentication methods come up short, and how to achieve passwordless the right way.













